Unggulan
- Dapatkan link
- X
- Aplikasi Lainnya
Nist 800 Risk Assessment Template - Risk Management Framework Rmf An Overview Varonis : This is the newest place to search, delivering top results from across the web.
Nist 800 Risk Assessment Template - Risk Management Framework Rmf An Overview Varonis : This is the newest place to search, delivering top results from across the web.. The risk report identifies all areas of risk collected in each section of the assessment. In compliance manager, go to your assessment templates page. You'll see a list of all the templates available to your organization. Security audit plan (sap) guidance. Acquisition assessment policy identification and authentication policy
In compliance manager, go to your assessment templates page. Based on the results of risk assessments can lower the number of incidents, but not all incidents can be prevented. The information technology laboratory (itl) at the national institute of standards and technology (nist) promotes the u.s. Published as a special document formulated for information security risk assessment, it pertains. •by first understanding the business and technical characteristics that impact system risk, an agency can identify and align controls to a component based on the likelihood that a weakness will be exploited and the potential impact to

December 15, 2019 by admin.
21 posts related to nist sp 800 30 risk assessment template. The pram is a tool that applies the risk model from nistir 8062 and helps organizations analyze, assess, and prioritize privacy risks to determine how to respond and select appropriate solutions. Use the modified nist template. Find content updated daily for template risk assessment You'll see a list of all the templates available to your organization. Computer security incident handling guide. The risk report identifies all areas of risk collected in each section of the assessment. List the risks to system in the risk assessment results table below and detail the relevant mitigating factors and controls. Cybersecurity risk assessment (cra) template. Identify the scope of the assessment; An incident response capability is therefore necessary for. The information technology laboratory (itl) at the national institute of standards and technology (nist) promotes the u.s. Risk profiling overview •risk profiling is a process that allows nist to determine the importance of a system to the organization's mission.
Cybersecurity risk assessment (cra) template. • it consultants, who support clients in risk management. Recommendations of the national institute of standards and technology. This is the newest place to search, delivering top results from across the web. Risk profiling overview •risk profiling is a process that allows nist to determine the importance of a system to the organization's mission.
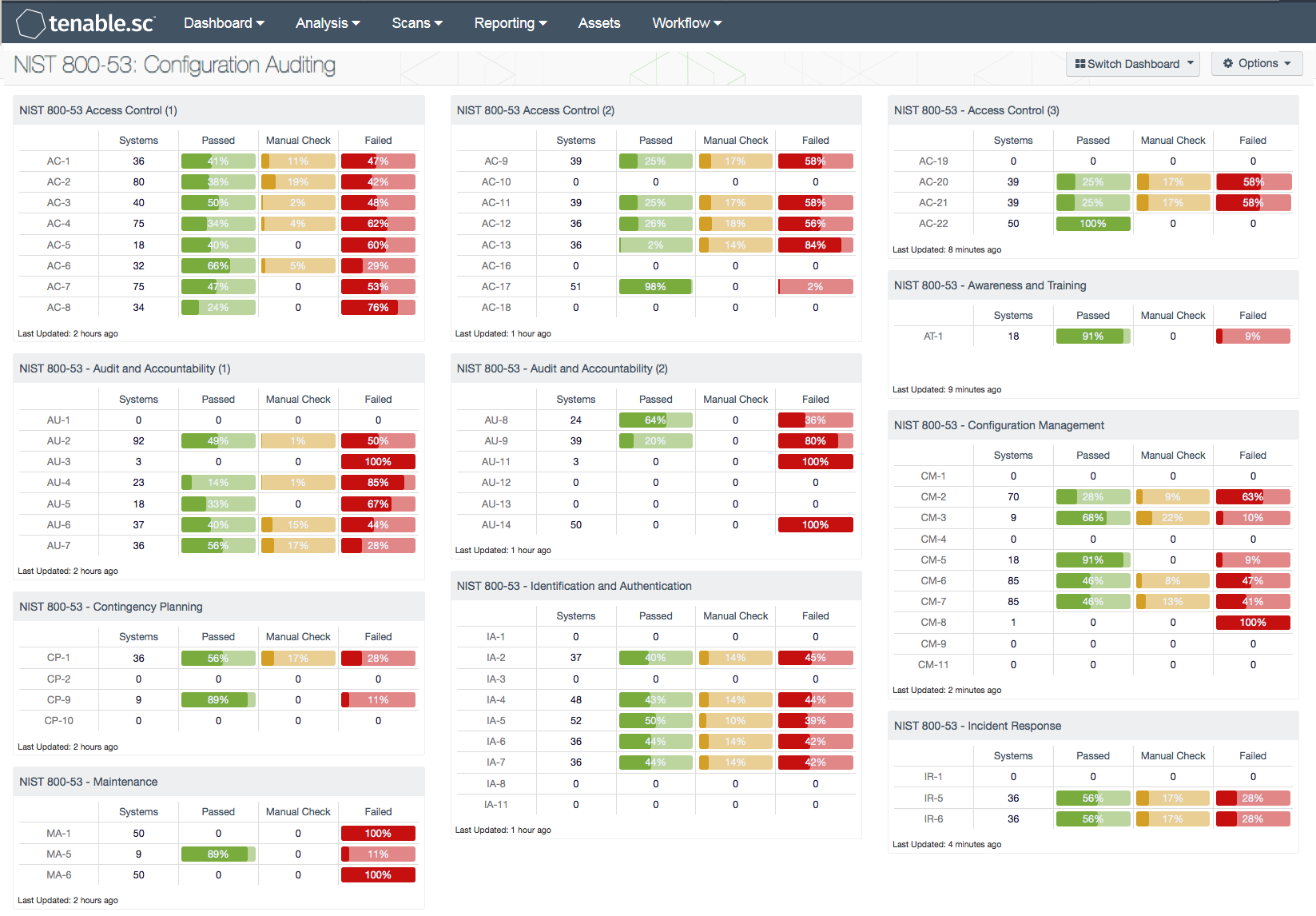
The risk assessment gui dance in special
Risk assessments, carried out at all three tiers in the risk management hierarchy, are part of an overall risk management process—providing senior leaders/executives with the information. Published as a special document formulated for information security risk assessment, it pertains. The following tasks are critical to performing a thorough risk assessment according to the special publication: The information technology laboratory (itl) at the national institute of standards and technology (nist) promotes the u.s. You'll see a list of all the templates available to your organization. Acquisition assessment policy identification and authentication policy Find content updated daily for template risk assessment Conduct and score the basic assessment. In compliance manager, go to your assessment templates page. Risk assessment approach determine relevant threats to the system. Use the modified nist template. List the risks to system in the risk assessment results table below and detail the relevant mitigating factors and controls. The risk assessment gui dance in special
Risk assessment methodology summary 13 13 risk assessment standards (e.g. However, any organization with poa&ms will want to reassess and update their ssps to achieve the best possible score. •by first understanding the business and technical characteristics that impact system risk, an agency can identify and align controls to a component based on the likelihood that a weakness will be exploited and the potential impact to • it consultants, who support clients in risk management. Each vulnerability selected is shown here along with each response sorted into areas for review.

Each vulnerability selected is shown here along with each response sorted into areas for review.
This is the newest place to search, delivering top results from across the web. Use the modified nist template. You'll see a list of all the templates available to your organization. Acquisition assessment policy identification and authentication policy • it consultants, who support clients in risk management. Recommendations of the national institute of standards and technology. However, any organization with poa&ms will want to reassess and update their ssps to achieve the best possible score. List the risks to system in the risk assessment results table below and detail the relevant mitigating factors and controls. Security audit plan (sap) guidance. Conduct and score the basic assessment. The cra supports the rmp product in answering the how? questions for how your company manages risk. The pram is a tool that applies the risk model from nistir 8062 and helps organizations analyze, assess, and prioritize privacy risks to determine how to respond and select appropriate solutions. Identify the scope of the assessment;
- Dapatkan link
- X
- Aplikasi Lainnya
Postingan Populer
Nachträgliche Glückwünsche Zum 50 Hochzeitstag : Glückwünsche Zum Geburtstag Und Hochzeit, Ffschwoich ... : Eingestellt von randellhintze um 16:59.
- Dapatkan link
- X
- Aplikasi Lainnya
Ariana Grande Dangerous Woman - Ariana Grande - Dangerous Woman Lyrics : 10 on the billboard hot 100.
- Dapatkan link
- X
- Aplikasi Lainnya
Komentar
Posting Komentar